Identity lifecycle and governance at the speed of business
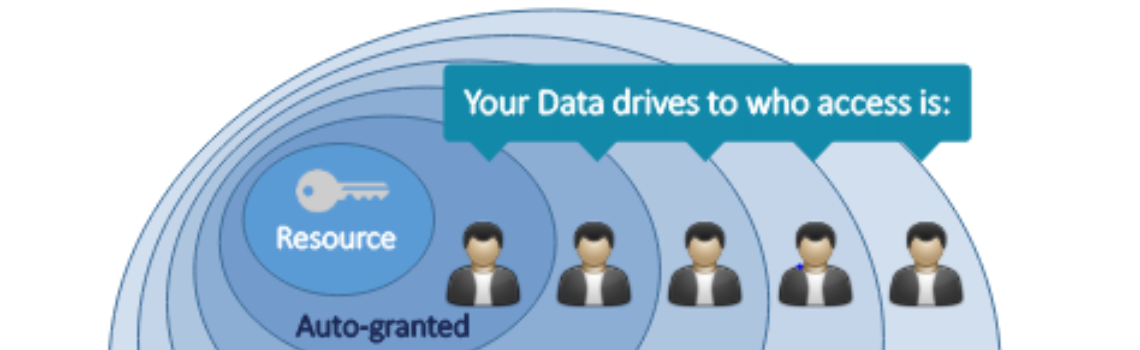
Full visibility and control over the access to applications and data in your digital landscape is becoming a necessity for any company. Achieving this is now possible through a single pane of glass by using Okta. Being a cloud-first product, Okta provides unprecedented speed through automations and brings ease of maintenance in the Identity Governance [...]
Lees verder