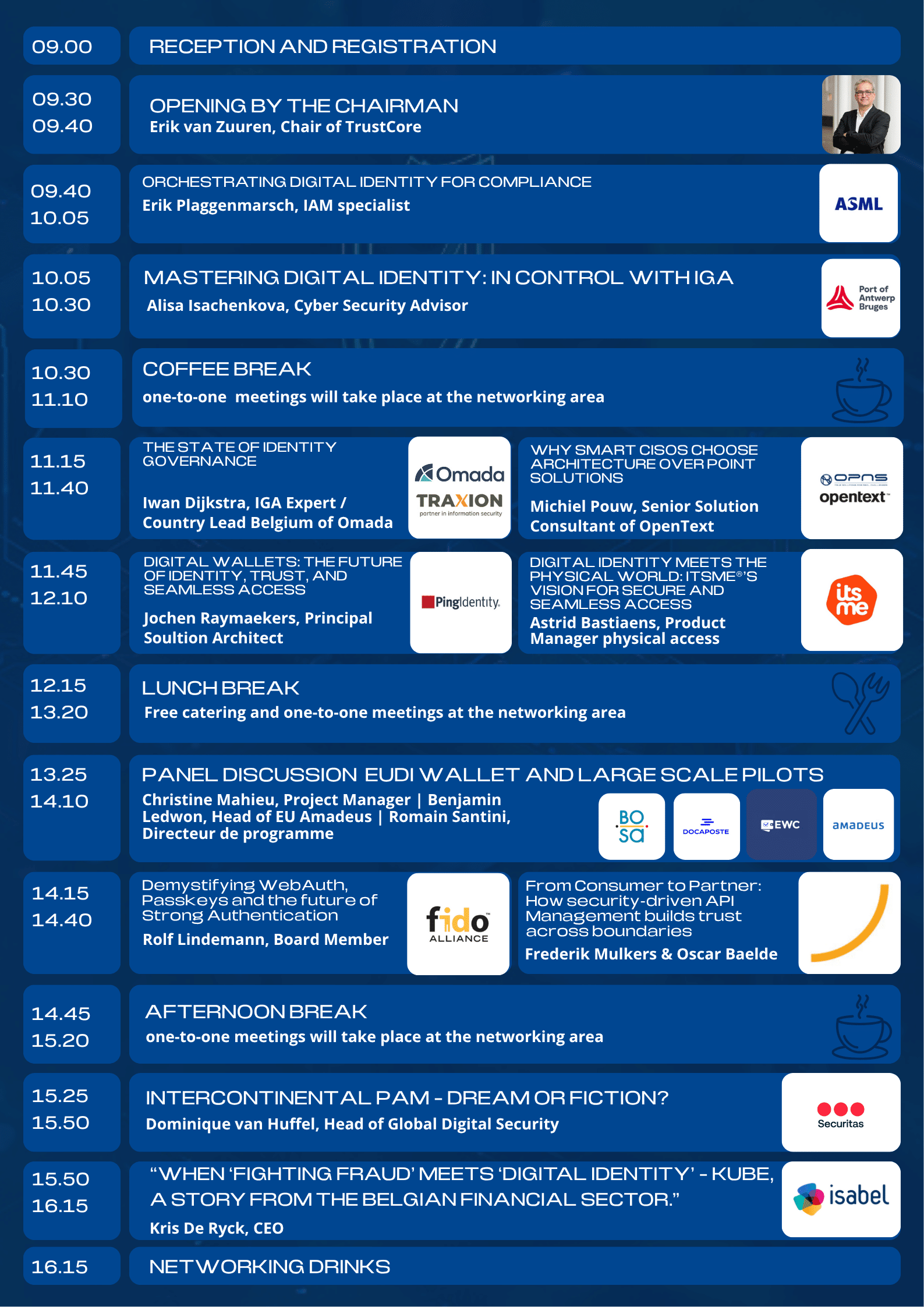
This is the programme of 2025
Digital Identities in the Age of AI and Digital Wallets
The Digital Identity & Trust Conference 2025 promises an exceptional program that brings together Europe’s leading experts in security standards with compelling local stories from Belgium.
Meet registered peers and solution providers from, among others, Deutsche Bank Belgium, Belfius Bank, Fluvius, OMP Belgium, Ping Identity, Port of Antwerp- Bruges, ASML, Okta, TUC Rail, UCB Biopharma, YPTO, SITS Traxion, Upright Security, Securitas, Isabel Group, Itsme, OPNS, Opentext, Omada, Docaposte, Amadeus, EWC, FIDO Alliance, Trend Micro & more.

Reception and Registration
Welcome to the Digital Identity & Trust Conference 2025. Upon registration, you will receive an SMS with your login link to Eventmanager. There, you can find your schedule and planned one-to-one meetings. Grab a cup of coffee or tea at the networking area, and enjoy your day!

Erik R. van Zuuren
CHAIRMAN OF THE CONFERENCE
Opening by chairman of the day
Erik van Zuuren, Chair of TrustCore
Chairman of the day Erik van Zuuren will open the programma and walk you trough what the day will bring.


Erik Plaggenmarsch
Domain Architect IAM of ASML
Orchestrating Digital Identity for Compliance
Erik Plaggenmarsch, Domain Architect IAM from ASML Netherlands
In today’s complex enterprise environments, identity has become the backbone of security and compliance. At ASML, one of the world’s leading technology innovators, Identity & Access Management is no longer an isolated discipline but an integrated ecosystem spanning Identity Governance, Access Management, PAM and Cryptography for humans and machines.
In this session, Erik Plaggenmarsch will share how ASML approaches Digital Identity Orchestration: aligning policies, organization and technologies to comply with regulations that apply to all sectors in the organization. This includes building adaptive access policies, embedding Zero Trust principles and enforcing export-control requirements into daily operations to stay compliant.
Expect a practical, no-nonsense view on how identity, upcoming technologies, compliance and security can be orchestrated together – offering insights that resonate for any organization dealing with scale, complexity, and regulatory demands.


Alisa Isachenkova
Cyber Security Advisor of Port of Antwerp-Bruges
Mastering Digital Identity: in control with IGA
Alisa Isachenkova, Cyber Security Advisor of Port of Antwerp-Bruges
In today’s rapidly evolving digital world, identity management is no longer a nice-to-have—it’s a critical foundation for security and compliance. This dynamic session dives into the transformative power of Identity Governance & Administration (IGA) and how it can help organizations reduce manual workloads, tighten access controls, and stay aligned with regulations like NIS2.
Discover how to align identity processes with your enterprise architecture and design a scalable roadmap for onboarding applications. We’ll explore proven practices in role modeling, stakeholder engagement, and change management that drive adoption and long-term success.
Packed with real-world insights and actionable strategies, this session will equip you with the tools and vision to build a future-ready identity strategy.


Morning Break at The Network Square With 1-to-1 Meetings
Enjoy fresh coffee, tea and snacks on the network square. And the first 1-to-1 meetings take place. Check your EventManager for your personal programme.

Iwan Dijkstra
IGA Expert / Country Lead Belgium - Omada of Omada
The State of Identity Governance
Iwan Dijkstra, IGA Expert / Country Lead Belgium of Omada
In this session, we’ll walk through the key findings from Omada’s annual research report, explore the main and actual business drivers for Identity Governance & Administration (IGA), and share real-world examples of what to consider before starting your IGA journey.



Toon van den Bergh
Account Manager of OpenText
The $2M Integration Trap: Why Smart CISOs Choose Architecture Over Point Solutions
Toon van den Bergh, Account Manager of OpenText
Every week, another CISO discovers the hidden truth about “best-of-breed” IAM strategies: that sleek MFA tool doesn’t talk to your governance platform, your SSO only works for cloud apps, and your users now navigate three different portals just to do their jobs.
The Real Question Isn’t “What’s the Best IAM Tool?”—It’s “How Do I Avoid the Integration Trap?”
In this dynamic 20-minute session, you’ll discover why the fastest path to IAM improvement often becomes the most expensive mistake—and what industry leaders are doing differently.
You’ll Learn:
- Why point solutions create more problems than they solve (real customer story included)
- The hidden costs of IAM fragmentation that hit 18 months after deployment
- How to protect 15+ years of IAM investment while modernizing to cloud
- The competitive advantage of “breadth-first” architecture over “best-of-breed” assembly
- Strategic questions to ask vendors that reveal integration reality vs. demo magic


Jochen Raymaekers
Principal Solution Architect, Ping Identity
Digital Wallets: The Future of Identity, Trust, and Seamless Access
Jochen Raymaekers, sr. Principal Soultion Architect, Ping Identity
Digital wallets are transforming identity by enabling secure, frictionless, and privacy-first experiences.
This session explores the drivers of adoption—from regulatory momentum to user demand—and the role of open standards in building trust.
Attendees will learn how digital wallets reduce fraud, strengthen compliance, and unlock new customer and workforce experiences, while preparing their organizations for the future of identity.


Astrid Bastiaens
Product Manager physical access of itsme Digital ID
Digital identity meets the physical world: Itsme®’s vision for secure and seamless access
Astrid Bastiaens, Product Manager physical access of itsme Digital ID
Digital identity is moving beyond online services into the physical world. In this session we outline Itsme®’s vision for Physical Access and show how it can create real impact. From ports and critical infrastructure to events and office buildings, we explore concrete use cases where trust and security meet convenience.
Rather than adding complexity, a unified approach to access makes life easier for end users while strengthening control for organizations. By connecting the digital and physical worlds, digital identity can open doors in more ways than one. This session offers both a glimpse of what is possible today and a vision of where digital identity can take us next.


Lunch Break at the Network Square with 1-to-1 Meetings
Enjoy your lunch at the networking square. During lunch there is enough time for 1-on-1 meetings and networking with colleagues, solution providers, peers and speakers.

Romain Santini
Director – Wallets offers & partnerships of Docaposte

Benjamin Ledwon
Director- Wallets offers & Partnerships

Christine Mahieu
Project Manager of FOD Beleid en Ondersteuning (BOSA)
Impact on the Private Sector and Use Cases for the EUDI Wallet
Romain Santini | Benjamin Ledwon | Christin Mahieu | Moderated by Erik van Zuuren
The European Digital Identity (EUDI) Wallet is set to reshape the private sector by enabling secure identity verification and the exchange of so-called electronic attestations of attributes. For businesses, this means more efficient customer onboarding, reduced fraud risk, and increased consumer trust.
From instant identity checks in banking to simplified checkouts in e-commerce and secure remote signing of contracts, the EUDI Wallet presents a wide range of practical applications. But what does this mean in practice?
Europe has already invested—and continues to invest—tens of millions of euros in large-scale pilot projects such as POTENTIAL, EWC, WEBUILD and APTITUDE. This session will explore the early findings of these pilots, what has worked, what remains challenging, and what the next wave of pilots aims to achieve.
Join us for a forward-looking discussion on how the EUDI Wallet could unlock real value for the private sector.


Rolf Lindemann
FIDO Board Member of FIDO Alliance
Demystifying WebAuth, Passkeys and the future of Strong Authentication
Rolf Lindemann, FIDO Board Member of FIDO Alliance
Rolf Lindemann will cut through the complexity of WebAuth and Passkeys, showing how they reshape the way we think about secure authentication. With deep expertise in digital identity and strong authentication, he makes future-proof security strategies tangible and practical. Expect clear insights into what’s next for user-friendly, phishing-resistant login experiences.


Frederik Mulkers
IT Architect of Onafhankelijke Ziekenfondsen - Mutualités Libres

Oscar Baelde
Integration Consultant of I8C
From Consumer to Partner: How security-driven API Management builds trust across boundaries
Frederik Mulkers, IT Architect of Onafhankelijke Ziekenfondsen - Mutualités Libres & Oscar Baelde, Integration Consultant of I8C
In a complex ecosystem of health insurance funds, 3rd party insurers, partners and their clients (insured persons), and government institutions, secure data exchange is not just a technical challenge—it’s a trust enabler. This session explores how federated identity, scoped access tokens, and tailored APIs per consumer type ensure that sensitive data flows securely and compliantly across organizational boundaries.
You’ll discover how API Management acts as the backbone of this architecture, enabling fine-grained access control, threat detection using STRIDE, and enforcement through smart policies. We’ll move from theory to practice with concrete examples of how authentication, audit trails, data masking, and throttling are used to mitigate real-world threats.
If you’re building or securing APIs in a regulated or multi-stakeholder environment, this session will equip you with actionable insights on designing trust into your API landscape


Afternoon break at the networking square with 1-to-1 meetings
Enjoy fresh coffee, tea and snacks on the network square. The last 1-to-1 meetings will take place. After this you get to enjoy the closing key-notes and networking drinks.

Dominique van Huffel
Head of Global Digital Security
Intercontinental PAM – dream or fiction?
Dominique van Huffel, Head of Global Digital Security of Securitas
From business case to effectively rolling out privileged access management is easier written than done. Performing this in an intercontinental organisation, 55 entities wide and on a mission to actively measure risk posture increase is a whole different ball game. During this session, we touch on the concepts, challenges and lessons learned on how Securitas drives Privileged Access Management in Core IT, Industrial IT and its business applications.


Kris de Ryck
CEO of Isabel Group
“When ‘Fighting fraud’ meets ‘Digital identity’ – KUBE, a story from the Belgian financial sector.”
Kris de Ryck, CEO of Isabel Group
“A robust Know-Your-Customer (KYC) management is essential for trust, compliance and fraud prevention. But let’s face it, it is also a real pain for financial players and their corporate customers. Designed as a unique community driven solution, Kube® not only drives down the administrative KYC burden but also creates the basis for a genuine Corporate passport.”


Networking drinks & appetizers
While enjoying a drink and snack, we close the day in an appropriate way. Discuss what you have learned with colleagues, peers and speakers.
Who will be speaking?
View our confirmed experts
Curious as to who will speak and what experience they bring? Quickly view our complete expert overview!