Recorded Future Intelligence Cloud: Know what matters. Act first.
2025 Global Threat Report
Reflections on the State of Cyber Security Sweden 2024: A Day of Insights and Innovation
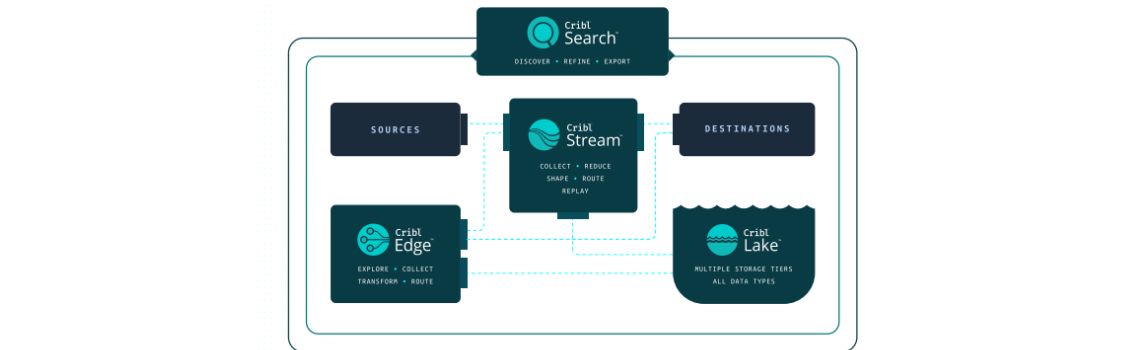
Cribl Solution Brief
Network and Information Security (NIS2) What the new EU directive means for corporate cybersecurity
Access control is an essential part of the NIS2 Directive. This is intended to significantly improve the security of network and information systems in the EU. It means that only authorised persons or devices can access the data or resources they need, and that unauthorised access is prevented or detected.
Cybersecurity in Sweden: Jesper Larsson on Emerging Threats and the Future of Security
As we gear up for the State of Cyber Security conference in Stockholm this December, cybersecurity experts and enthusiasts alike are excited to hear from keynote speaker Jesper Larsson. With his vast experience in offensive security and his notable contributions to the Swedish tech scene, Jesper is a name many in the industry recognize, whether […]
Whitepaper: All Eyes on Cloud Why the Cloud Surface Attracts Attacks
Over the past decade, cloud environments have experienced exponential growth. Initially conceived as a solution for data storage, they have evolved into comprehensive computing platforms, revolutionizing how businesses handle information globally. However, with this transformation,
Whitepaper: Five Best Practices for CISOs Adopting XDR
The adoption of Extended Detection and Response (XDR) presents significant opportunities for Chief Information Security Officers (CISOs) to enhance their organization’s cybersecurity posture. When considering XDR implementation, CISOs should prioritize a strategic approach that encompasses
Whitepaper: The Complete Guide to Enterprise Ransomware Protection
Protecting against ransomware is crucial in today’s digital landscape. This white paper will offer you valuable insights, recommendations, and real-world examples to help you understand, prepare for, and respond to this prevalent threat. Learn how to safeguard your data, mitigate the risks
- 1
- 2