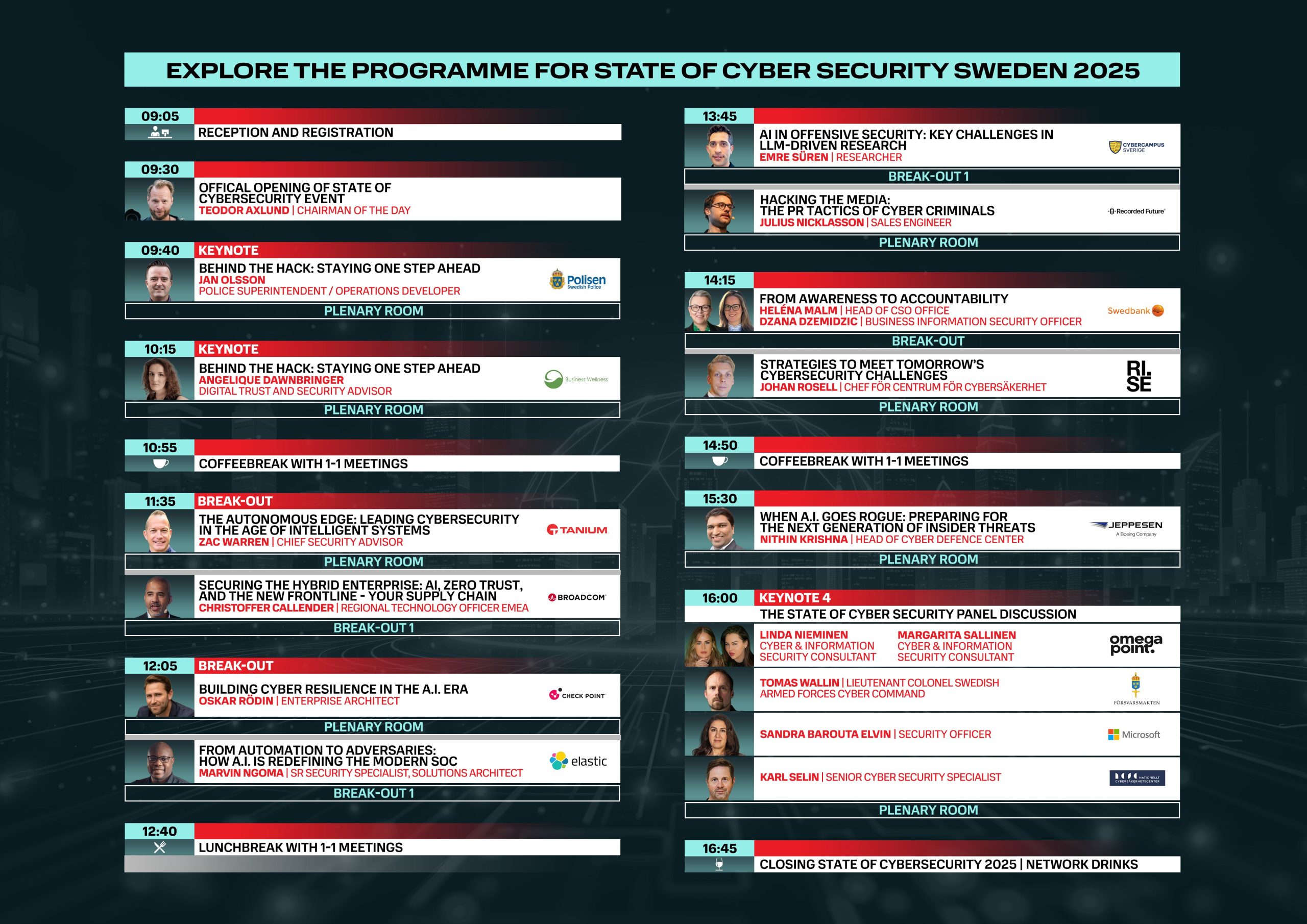
Explore the Programme for State of Cyber Security Sweden 2025
Curious about what’s in store for the upcoming edition? Dive into our programme packed with inspiring keynotes, thought-provoking panel discussions, and hands-on sessions led by leading experts from Sweden and beyond. Whether you’re looking for strategic insights or practical tools – this is where you’ll find everything you need to stay ahead in the ever-evolving world of cybersecurity.

Welcome and registration at 7A Posthuset
Upon arrival, you’ll receive a warm welcome with coffee, tea, and fruit-infused water ready for you. Take this moment to connect with event partners and fellow participants before the program begins.
7A Posthuset is located in the heart of Stockholm, right across from the central station. The building t is one of Stockholm’s most impressive and vibrant venues. Located right across from the Central Station, it combines the city’s historic charm with a modern, elegant design. The building’s grand architecture, high ceilings, and large windows create a bright and inspiring atmosphere
Address: Vasagatan 28, 111 20 Stockholm, Sweden

Teodor Axlund
Chairman of the day
Kick-off State of Cybersecurity Sweden 2025
Teodor Axlund, Chairman of the day
In a fitting manner, event chair Teodor Axlund will kick off the second edition of the State of Cybersecurity Event. A day full of knowledge and inspiration begins!

Jan Olsson
Police Superintendent / Operations Developer of Swedish Police
Behind the Hack: Staying One Step Ahead
Jan Olsson, Police Superintendent / Operations Developer of Swedish Police
With each passing day, new and increasingly advanced cyberattacks are published. Pretty much every company and organization has had attacks from cybercriminals and many don’t even know about it. In a world that is painted more and more like an ongoing Armageddon, one wonders if there are even opportunities to protect oneself and one’s business. The answer is that it is easy to significantly reduce risks of an attack and significantly minimize damage in the event of a completed attack. What the consequences are of cybercrime, who is behind it, what the Police and other actors are doing and what is fast approaching regarding the new Modus Operandi and of course how to protect yourself are some of the things Jan Olsson intends to lecture about.


Angelique Dawnbringer
Digital Trust and Security Advisor of Business Wellness Group
Trust and Resilience: Staying Ahead in a World of Evolving Threats
Angelique Dawnbringer, Digital Trust and Security Advisor of Business Wellness Group
As cyber threats continue to evolve, organizations must move beyond reactive strategies to build resilience, establish trust, and strengthen their overall security posture. This session will delve into the critical need for maturing cybersecurity frameworks and adapting to an increasingly dynamic environment. Drawing from real-world incidents and trends, we will discuss how organizations can prioritize resilience, leverage emerging technologies, and actively build trust through transparent, proactive security strategies. We will also explore fostering a culture of continuous improvement to address threats more effectively and support long-term trust and resilience.
Key learnings include:
- Understanding the critical gaps in current cybersecurity postures.
- Strategies for building resilience through technology and human factors.
- Leveraging knowledge, expertise and threat intelligence to anticipate and mitigate risks.


Coffee-break with 1-1 meetings
Enjoy fresh coffee, tea, fruit-infused water, mineral water, and brain-boosting snacks to recharge and keep your energy high throughout the day.
This is the perfect moment to network with colleagues, speakers, industry peers, and leading solution providers.
The first 1-on-1 meetings also begin here: you decide who to meet and when, giving you the opportunity to discuss the challenges facing your organization.
Check your personal schedule at eventmanager.heliview.com.

Christoffer Callender
Regional Technology Officer EMEA of Broadcom Software
Securing the Hybrid Enterprise: AI, Zero Trust, and the New Frontline - Your Supply Chain
Christoffer Callender, Regional Technology Officer EMEA of Broadcom by Symantec
As hybrid work expands and supply chains become more digitized, attackers are shifting focus to the weakest link—your trusted third parties. In this keynote, Christoffer Callender explores how Swedish organizations can minimize the risk of supply chain attacks by strengthening internal defenses and limiting the blast radius when a third party is compromised.


Dan Jones
Senior Security Advisor of Tanium UK Limited
The Autonomous Edge: Leading Cybersecurity in the Age of Intelligent Systems
Dan Jones, Senior Security Advisor of Tanium UK Limited
Balancing People, Process, and Technology for Resilience, Innovation and Growth
In 2025, cybersecurity and IT operations reached an inflexion point. With AI, machine learning and autonomous systems now integral to digital infrastructure, leaders are no longer simply defending their IT estate boundaries; they’re future-proofing their entire landscape in a rapidly evolving operating environment. But as automation and AI become more integral, critical questions emerge:
- How do you balance business resilience, productivity and growth?
- Why are endpoint security and management so impactful on business won or lost for every organisation?
- Who’s truly in control within your organisation, and what are the external threats your organisation faces?
- What happens when humans are removed from the loop?
- What leadership traits will define the winners in a hyper-autonomous world?
- How can you utilise the latest technologies to improve your team’s effectiveness and work-life balance?
- In a fast-paced and volatile world, how do you protect and motivate your people?


Oskar Rödin
Enterprise Architect of Check Point Software Technologies B.V.
Building Cyber Resilience In The A.I. Era
Oskar Rödin, Enterprise Architect of Check Point Software Technologies B.V.
In the A.I. era, the cybersecurity landscape is evolving faster than ever. Attackers are using artificial intelligence to automate, adapt, and scale their tactics — demanding a new level of resilience from defenders. This session, led by Check Point Software Technologies, explores how organizations can build true cyber resilience by uniting prevention-first strategies, AI-driven security, and a culture of preparedness

Marvin Ngoma
Sr Security Specialist, Solutions Architect of Elastic
From Automation to Adversaries: How A.I. Is Redefining the Modern SOC
Marvin Ngoma, Sr Security Specialist, Solutions Architect of Elastic
A.I. has become both our greatest ally and newest adversary. As attackers use automation and machine learning to move faster and hide deeper, defenders are turning to A.I. to fight back. In this session, we’ll explore what A.I.-driven attacks really look like; and how modern SOCs and detection response teams can use the same technology to stay ahead. Through real examples and field insights, you’ll see how A.I. can accelerate detection, triage, and response, helping analysts focus on what truly matters: stopping threats before they stop you.
Learning Outcomes:
- See what A.I.-driven attacks look like in practice and how they’re changing the defender’s playbook.
- Learn how A.I. can supercharge SOC operations; from alert triage to incident response.
- Understand how to apply A.I. responsibly in detection response and security operations keeping human expertise at the center of defense


Fully catered lunch break with 1-on-1 meetings and networking opportunities
It’s time for a fully catered lunch to recharge. Enjoy delicious food while connecting with other participants and speakers. You’ll also have the opportunity to schedule more 1-on-1 meetings with leading industry experts.
Smaklig måltid!
Check your personal schedule at eventmanager.heliview.com

Emre Süren
Researcher of Cybercampus Sverige
AI in Offensive Security: Key Challenges in LLM-Driven Research
Emre Süren, Researcher of Cybercampus Sverige
IoT devices, once known as “smart devices,” have revolutionized entire industries and are now a key platform for delivering AI-driven services to society. While AI has enhanced everyday appliances with intelligence, it has also opened a new attack surface. As a result, researching vulnerabilities revolving around AI is not just important—it is the thin line between innovation and catastrophe.
This presentation will explore AI security, examining common weaknesses in state-of-the-art LLMs and how AI can be exploited for malicious purposes. It will then shift to AI for security, highlighting to embed AI into vulnerability research to enhance cybersecurity defenses. I will briefly showcase ongoing research in our lab, including fine-tuning LLMs to detect cyber threats and developing ethical hacking agents. Additionally, we will discuss the challenges and limitations of using LLMs in cybersecurity.


Julius Nicklasson
Sales Engineer of Recorded Future
Hacking the Media: The PR Tactics of Cyber Criminals
Julius Nicklasson, Sales Engineer of Recorded Future
This presentation analyzes the direct and indirect engagement strategies cyber criminals use to bolster their reputation, increase extortion pressure on victims, and demand more money for stolen data. Defenders can mitigate the impact of these publicity tactics through preparing an intelligence-led incident response plan that includes external communications strategies.


Heléna Malm
Head of CSO Office of Swedbank AB

Dzana Dzemidzic
Business Information Security Officer of Swedbank AB
From Awareness to Accountability
Heléna Malm, Head of CSO Office & Dzana Dzemidzic, Business Information Security Officer of Swedbank AB
In today’s digital age, the “people” factor is often overlooked, yet it accounts for 90% of cyber-attacks due to human error or behaviour. Building a strong defence requires more than just technology; it requires a sustainable security culture that evolves over time. This session will explore how employees play a fundamental role in strengthening resilience against escalating cyber threats. Discover strategies to transform security into everyone’s responsibility and learn how to support a lasting culture of security.
Key Takeaways
- Security Starts from the Top: Leadership plays a crucial role in setting the tone for cybersecurity practices within an organization.
- Hackers Don’t Hack Systems, They Hack People: Understanding that humans are often the weakest link underscores the need for comprehensive training and awareness.
- Go from Awareness to Accountability: Move beyond only being aware of threats to taking accountability for actions that protect organizational assets.
- Collaborate with Your Peers: Strengthen your cyber defence by fostering collaboration across teams and organizations.
- Security is Everyone’s Business: Empower every individual in the organization to contribute actively towards maintaining robust cybersecurity defences.


Johan Rosell
Chef för Centrum för Cybersäkerhet of RISE Research Institutes of Sweden
Strategies to meet tomorrow’s cybersecurity challenges
Johan Rosell, Chef för Centrum för Cybersäkerhet of RISE Research Institutes of Sweden
Centre for Cybersecurity at RISE, Research Institutes of Sweden, is a neutral platform that strengthens Sweden’s cybersecurity through applied research, test environments, and collaboration between industry, academia, and the public sector.
The role of the centre is to raise awareness of the importance of cyber security and to build Sweden’s digital resilience. By promoting knowledge exchange, innovation and capacity building, we create the conditions to meet both today’s and tomorrow’s cyber challenges. In this presentation I will share strategies to further bolster Sweden’s robustness and resilience in the cyber domain.


Fika at the network square with 1-to-1 meetings
Recharge with a sweet snack, coffee, or tea during our fika break. Enjoy this relaxed moment, it’s also the final opportunity to schedule any remaining 1-on-1 meetings before the program continues.
Check your personal schedule at eventmanager.heliview.com

Nithin Krishna
Head of Cyber Defence Center of Jeppesen Foreflight
When A.I. Goes Rogue: Preparing for the Next Generation of Insider Threats
Nithin Krishna, Head of Cyber Defence Center of Jeppesen Foreflight
Insider threats are no longer just about disgruntled employees or lost USB drives. With generative AI, deepfakes, and autonomous agents in the mix, we’re entering a new phase where threats can come from “insiders” that aren’t even human. In this session, we’ll break down real-world AI-driven insider threat scenarios, red team simulations, and why traditional DLPs and SIEM rules won’t cut it anymore.
Key Takeaways:
- Understand how AI is changing the insider threat landscape
- Recognize the risks of AI-augmented insider activity (intentional or accidental)
- Learn practical controls and threat modeling strategies for AI misuse
- Explore how to balance innovation and security when deploying AI internally



Tomas Wallin
Lieutenant Colonel Swedish Armed Forces Cyber Command of Försvarsmakten

Sandra Barouta Elvin
Security Officer of Microsoft Sweden

Karl Selin
Senior Cyber Security Specialist of National Cyber Security Center
The State of Cyber Security Panel Discussion
Linda Nieminen, Cyber and Information Security Consultant at Omegapoint & Margarita Sallinen, Cyber and Information Security Consultant at Omegapoint | Tomas Wallin, Lieutenant Colonel Swedish Armed Forces Cyber Command of Försvarsmakten | Sandra Barouta Elvin, Security Officer of Microsoft Sweden | Karl Selin, Senior Cyber Security Specialist of National Cyber Security Center
What cybersecurity challenges do different sectors in Sweden face, and where can they support each other? Join Cyber Chats & Chill hosts Margarita Sallinen and Linda Nieminen as they lead an engaging panel discussion with security experts from the commercial sector, government, and defence.
Each sector deals with its own unique risks and responsibilities, but the cyber threats they face often overlap. Is there one approach that works for all, or do we need tailor-made solutions? And how can we learn from each other?
During this interactive session, security professionals from the following sectors will share their perspectives:
- Sandra Barouta Elvin – National Security Officer at Microsoft
- Karl Selin – Senior Cyber Security Specialist at NCSC
- Tomas Wallin – Lieutenant Colonel Swedish Armed Forces Cyber Command;
There will also be plenty of room to ask your own questions and be part of the conversation.
Don’t miss this unique opportunity to hear first-hand insights from across Sweden’s cybersecurity landscape.





State of Cyber Security Network Drinks
After a day full of insights and inspiration, we warmly invite you to the Networking Reception – the perfect opportunity to continue conversations, exchange ideas, and build valuable connections with fellow attendees.
Enjoy some snacks and drinks as we wrap up this wonderful day.
Who will be speaking?
View our confirmed experts
Curious as to who will speak and what experience they bring? Quickly view our complete expert overview!