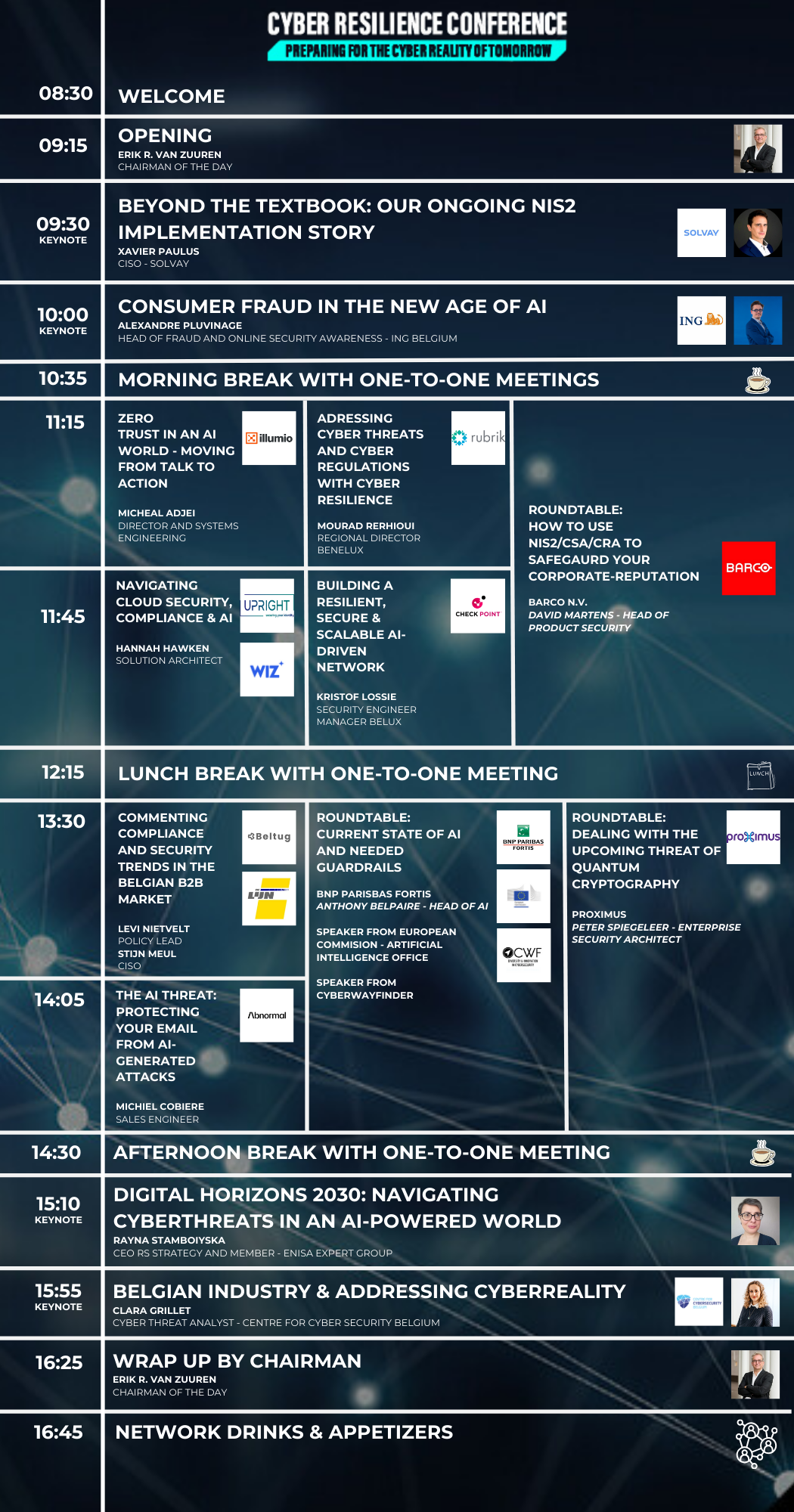
Programme
Preparing for the Cyber Reality of Tomorrow
Everyone in the IT or security industry is living in very interesting yet challenging times. On the one hand we live in times where new technologies create vast new possibilities, on the other hand the rapid paces makes it very difficult to keep up and stay in control.
How can we prepare for tomorrow and keep our organizations safe? Start with by learning from peers and discussing strategies for keeping things under control. So, join the Cyber Resilience Conference, explore these innovations and build strong relationships to make your organization more secure and resilient!

WELCOME AND REGISTRATION
The Heliview employees will welcome you to the conference in Van der Valk Hotel **** in Mechelen. Parking at Parking Keerdok is accessible from the N16 via a direct exit lane. Via the bicycle and pedestrian bridge, you get to the Van der Valk hotel just a 2-minute walk away. The address to reach Parking Keerdok is Antonia Wolversstraat 1, Mechelen.
Of course the coffee or tea is ready for you!

Erik van Zuuren
Chair of TrustCore
Chairman of the day Erik R. van Zuuren
Erik is actively engaged in several professional activities. As such he founded TrustCore.EU, he executed several assignments private and public sector (European Commission, Federal Government, Flemish Government, Euroclear, Infrabel, Electrabel, BPost, ENISA, etc). Currently his main focusses are on the topics of Openbanking and Security Architecture at BNP Paribas Fortis as well as the wide topic of the new Trust Regulation en the European Digital Identity Wallet in collaboration with the EU Member States.
In his spare time, Erik is also Topic Leader “Security Architecture Management” at Solvay Brussels School and a member of the Vlaamse Toezichtcommissie (Flemish DPA). With his knowledge and experience, Erik is the ideal person to guide the conference as chair of the day

Xavier Paulus
CISO of Solvay
Keynote: Beyond the Textbook: Our ongoing NIS2 Implementation Story
Xavier Paulus, CISO, Solvay
This keynote offers a practical, experience-based account of our ongoing NIS2 implementation journey within a company undergoing significant structural change. It’s a candid reflection on our current progress, the challenges we continue to face, and the lessons we are still learning. We’ll cover key aspects, including initial assessment and stakeholder engagement, planning and pitfalls, navigating registration, and our evolving understanding of the core challenges and opportunities. Our implementation is a continuous learning process, and this presentation will honestly address the difficulties encountered, the adjustments made, and the insights gained. So come and join us in discussing concrete implementation of NIS2!


Alexandre Pluvinage
Head of Fraud and Online Security Awareness of ING
Keynote: Consumer fraud in the new age of AI
Alexandre Pluvinage, Head of Fraud and Online Security Awareness, ING
In today’s digital era, AI has revolutionized many aspects of our lives, but it has also opened new avenues for consumer fraud. This presentation by Alexandre Pluvinage, Head of Fraud and Online Security Awareness at ING Belgium will explore how AI is being exploited to deceive consumers, the types of fraud emerging, and the impact on individuals and businesses. We’ll also discuss strategies to protect against these sophisticated threats and ensure a safer digital marketplace. Join us to understand the challenges and solutions in combating consumer fraud in the age of AI. (note : this text has been created by AI).


MORNING BREAK AT THE NETWORK SQUARE WITH one-TO-one MEETINGS
Enjoy fresh coffee, tea and snacks on the network square, such as kako Cream, lactose-free Panna cotta, chocolate brownies and fresh fruit. The first one-to-one meetings will take place.

Michael Adjei
Director, Systems Engineering of Illumio
Break-out session A1: Zero Trust in An AI World – Moving From Talk to Action
Michael Adjei, Director and Systems Engineering, Illumio
In the face of evolving threat landscape, it is no longer a matter of if you are targeted by threat actors but rather when you are targeted.
This fact is further amplified by the pervasive use of AI across various digital platforms today. So, in this unpredictable era, how can organisations set themselves up to survive and thrive even after a cyber attack?
This session will focus on how to implement zero trust principles with ease and speed to ensure critical business operations can continue during and after a cyber incident
The session will cover:
- Rethinking cyber resilience in favour of ease of operationalisation
- Key considerations for an effective defence-in-depth strategy
- Insights for CISOs and security managers
- Pragmatic steps on business continuity through an adaptive security posture


Mourad Rerhioui
Regional Director Benelux of Rubrik B.V.
Break-out session A2: Addressing Cyber Threats and Cyber Regulations with Cyber Resilience
Mourad Rerhioui, Regional Director Benelux of Rubrik B.V.
In our rapidly evolving digital landscape, traditional cybersecurity strategies have predominantly focused on prevention, aiming to erect barriers against cyber threats. However, the complexity and sophistication of modern cyber attacks have revealed significant limitations in this approach. This session will explore the paradigm shift towards cyber resilience, emphasizing the critical need for organizations to not only prevent but also effectively respond to and recover from cyber incidents. We will delve into how current cyber investments have been skewed towards preventative technologies and discuss why this is no longer sufficient. With cyber threats becoming more pervasive and destructive, operational resilience – the ability to maintain essential functions during and after a cyberattack – has emerged as a key strategic imperative.
This session will cover:
- Cloud Security
- Compliance, Legislation & Regulation
- Governance & Risk Management
- Security Architecture & Technologies


David Martens
Chief Product Security Officer - Head of Product Security, Barco N.V.
Roundtable A3: Impact of EU cybersecurity regulations on a manufacturer of digital products
David Martens, Chief Product Security Officer - Head of Product Security, Barco N.V.
All of us have heard and read enough about NIS2 Directive and Cyber Security Act and Cyber Resilience Act. But what do these regulations really mean in practice? Where and how do they really apply? Next to be compliant, how can we use it to showcase our organization’s professionalism both at organizational level and at product level when you are a provider? Where and how can you use it as some “level of guarantee” as a consumer of services or products? As to get out of theory, we invited some experts of BARCO who have and are working on all of these fronts and to allow to hear their views and practical experience. I addition, this session will be in roundtable-mode allowing extra space to really engage with the speakers as well as all the participants in the roundtable.


Hannah Hawken
Solutions Architect of Wiz Cloud Limited
Break-out session B1: Navigating Cloud Security, Compliance & AI
Hannah Hawken, Solutions Architect of Wiz Cloud Limited
As organizations adopt multi-cloud and AI technologies at scale, security and compliance teams face new challenges: fragmented visibility, growing risk surfaces, and evolving regulations. In this session, we’ll explore a practical approach to managing these complexities using the principles of Cloud-Native Application Protection Platforms (CNAPP).
Attendees will learn:
- How to gain end-to-end visibility across multi-cloud environments
- Strategies to assess and reduce risk without disrupting development
- How to approach governance around AI usage and data access
- What a modern, scalable cloud security architecture looks like in practice



Kristof Lossie
Security Engineer Manager BeLux, Check Point
Break-out session B2: Building a Resilient, Secure & Scalable AI-Driven Network
Kristof Lossie, Security Engineer Manager BeLux, Check Point
We have entered the age of AI, where seamless and secure connectivity is the backbone of innovation. AI applications rely on real-time data exchange, AI models interact with each other, and users demand frictionless access. But how do we ensure resilience and security in this evolving landscape? At Check Point, we introduce the Hybrid Mesh Security Architecture—a flexible framework that provides robust protection while optimizing performance. This architecture enables secure connections across AI workloads, data sources, and users without compromising agility. Want to learn how to future-proof your AI-driven network? Join our session!


LUNCH BREAK AT THE NETWORK SQUARE WITH one-TO-one MEETINGS
During lunch our chef serves various bowls with bulgur, sweet potato or greek pasta with toppings such as salmon, crusted chicken, grilled halloumi, caviar of smoked eggplant, grilled green asparagus, edamame, sundried tomatoes and more. To end your meal you can choose a healthy dessert bowl, low in fat and sugar.

Stijn Meul
Beltug Security Task Force / CISO of De Lijn

Levi Nietvelt
Policy Lead and Bussiness Development of Beltug
Break-out session C1: Commenting Compliance and Security trends in the Belgian B2B market
Stijn Meul, Beltug Security Task Force / CISO, De Lijn and Levi Nietvelt, Policy Lead and Business Development, Beltug
Every 2 years, Beltug, together with several of its partners, collects information on the views and trends in the Belgian B2B market. The 2025 version questioned more than 1000 organisations and included compliance and security. Join this duo presentation by Levi and Stijn who is a Member of the Beltug Security Taskforce and CISO at De Lijn for this interactive session where you will learn about the findings and join a discussion on what it means in practice. Has compliance also positive aspects? What does it mean for resilience when more organisations declare to have a cyber incident response plan? And what about the smaller organisations relying almost completely on their cloud supplier for their cloud security? During this session, you will also be invited to provide your views.



Anthony Belpaire
Head of AI of BNP Parisbas Fortis

Luca Massarelli
Expert at European Commission - DG CONNECT – EU AI Office

Niklas Bunzel
AI security researcher of Fraunhofer SIT & Member of the OWASP AI Exchange
Roundtable C2: Panel: Current state of AI and needed Guardrails
Anthony Belpaire, Head of AI, BNP Parisbas Fortis
In this session we will explore together with our experts the increasingly accelerating use of AI in business. As such, participants can understand the reality some are already facing and others will most probably soon be facing. Next, we will explore the regulatory context by discussing the AI Act and what legal guardrails Europe proposes to keep European citizens safe and why this is needed. In addition, we invited security experts that worked on a framework to help security specialists to assess their organization’s mature and risks and build a security program For their AI-activities. This session will be in roundtable-mode allowing extra space to really engage with the speakers as well as all the participants in the room.




Peter Spiegeleer
Enterprise Security Architect of Proximus
Roundtable C3: Dealing with the Upcoming Threat of Quantum Cryptography
Peter Spiegeleer, Enterprise Security Architect, Proximus
Accelerating developments in the field of quantum computing will bring disruptive challenges to cybersecurity. Organizations will need to adapt to the risk posed by quantum computers, which will have the potential to break many of the cryptographic systems that we rely on today and that are nested largely and deeply in our infrastructure. We are at risk already right now, as encrypted communications are stored by attackers to be decrypted years later with quantum computers (aka “store-now-decrypt-later attack”). Migration to quantum-safe solutions is inevitable. National governments are urging the industries to prepare for “Post-Quantum Cryptography”. In this roundtable, we will objectivate the risk and discuss strategies. What is the sense of urgency? Is your company developing a policy and mobilizing teams? How to conduct a diagnosis? How to implement for crypto-agility? How to plan for migration? What about the supply chain risk? Join this roundtable together with your peers to gain new insights and to prepare for resilience against evolving cyber threats.


Michiel Corbiere
Systems Engineer of Abnormal Security
Break-out session D1: The AI Threat: Protecting Your Email from AI-Generated Attacks
Email security is at a turning point. The rise of generative AI is transforming the threat landscape, enabling attackers to craft hyper-personalised, convincing phishing emails at scale. Traditional defences—built to detect outdated attack patterns—are struggling to keep up. In this session, we’ll explore:
- The Evolution of Email-Based Attacks – How cyber threats have advanced and why AI is accelerating their effectiveness.
- The New Cybersecurity Reality – With 91% of security professionals reporting AI-enabled attacks in the last six months and 97% acknowledging that traditional defences are ineffective, how can we adapt?
- Good AI vs Bad AI – How attackers leverage AI to bypass defences, and why security teams need AI-driven solutions to fight back.
- Taking an Abnormal Approach to Cybersecurity – Real-world examples of AI-generated threats stopped by Abnormal Security, showcasing how behavioural AI can detect and block even the most sophisticated attacks.


AFTERNOON BREAK AT THE NETWORK SQUARE WITH one-TO-one MEETINGS
Enjoy the afternoon break at the network square with a sweet treat such as creme brûlée, tiramisu, strawberries with praline and fresh fruits. The last one-to-one meetings will take place, meet colleagues, peers and speakers and share your gained knowledge!

Erik van Zuuren
Chair of TrustCore
Welcome back by chair Erik R. Van Zuuren
Welcome back by chair Erik R. Van Zuuren

Rayna Stamboliyska
CEO RS Strategy and Member of ENISA Expert Group
Keynote: Digital Horizons 2030: Navigating Cyberthreats in an AI-Powered World
Rayna Stamboliyska, CEO RS Strategy and Member of ENISA Expert Group
This forward-looking presentation explores the evolving cybersecurity landscape through the lens of geopolitical dynamics and emerging technologies. Drawing from ENISA’s threat intelligence framework, Rayna’s talk examines how artificial intelligence and cyber warfare capabilities are reshaping national security paradigms. Key focus areas include the convergence of state-sponsored cyber operations with commercial threats, the weaponisation of emerging technologies, and the transformation of critical infrastructure vulnerabilities.
The presentation offfers strategic insights into preparing for future cyber challenges while highlighting the importance of international cooperation in building cyber resilience. Special attention will be given to the European cybersecurity posture and its role in shaping global cyber defense strategies towards 2030.

Clara Grillet
CyTRIS - Threat Research Centre - Cyber Threat Analyst of Centre for Cyber Security Belgium
Keynote: What is cyber reality today for the Belgian industry
Clara Grillet, CyTRIS - Threat Research Centre - Cyber Threat Analyst, Centre for Cyber Security Belgium
Cyber threats are increasing in Belgium, fueled by money and geopolitical tensions. Technological advances like AI aid threat actors to target Belgian organizations across sectors, company size and language barriers. With the cloud, the attack surface is rising dramatically. If the cyber reality in Belgium can be seen as bleak, there are also positive examples of defenses that work. Drawing on real-life incidents and Belgium-specific data collected by the Centre for Cybersecurity Belgium, Clara will show you what is really going on out there…from rising threats all the way to effective defenses. This talk will give you an overview of current and future cyber threats to Belgian organizations with a focus on concrete cases so that you are better equipped to make relevant and targeted decisions to improve your organization’s defenses.


Erik van Zuuren
Chair of TrustCore
Wrap up by chair Erik R. van Zuuren & Winner Helview & ISACA Cyber Resilience Award
Wrap up by chair Erik R. van Zuuren & Winner Helview & ISACA Cyber Resilience Award

Network drinks & appetizers
We end the day in an appropriate manner while enjoying a drink, appetizers and finger food. Have informal discussions with colleagues, peers, partners and speakers.
The place for security leaders to be & network
Cyber Resilience Conference is a strategic conference, specially developed for security managers and management. How can we prepare for tomorrow and keep our organizations safe? To start with by learning from peers and discussing strategies for keeping things under control. So, join the Cyber Resilience Conference to explore these innovations and build resilience!
Some of the functions from your peers who are joining this edition: CEO, CISO, DPO, Chief Security Officer, Access and Identity Manager, COO, Architect, CIS Security Manager, Security Officer, Cyber Security Manager, CyberSecurity Engineer, ITM/ PISO, Head of Cybersecurity and many more.
Meet some of the peers who are joining this year
European Commission, Finvision, Toyota Motor Europe, Azelis, G4S Security Services B.V., OMP Belgium, Federal Government, Vlaamse Overheid, Sociale Zekerheid Zelfstandige Ondernemers, Orange Belgium SA, EY Belgium, KBC Bank N.V., Bua Unlimited SRL, IBPT, Skytanking N.V., Federale Pensioendienst, Vanbreda Risk & Benefits, Vlaamse Radio en Televisieomroeporganisatie, Howest, University of Applied Sciences, Vivee cvba, Cegelec Fire Solutions, APK Group, DHL Express Europe Headquarters and many more!